Cyber Threats from China: Chinese Offensive Capabilities and Modus Operandi
China raised cyber war units way back in 20031. Major objectives of these units has been cyber surveillance, manipulating network data, disseminating propaganda, misinformation, deception, planting logic bombs in the target networks to be activated later, establishing network spy stations, organizing information defense, conducting distributed denial of services attack on the target networks. Besides, China is known for cyber espionage through citizen hacker groups as also by professional military hackers.
As an adjunct to the cyber war activities given above, China makes concerted efforts to manipulate international public opinion in its favour using its sharp power. A data leak revealed more than two million communist party officials working in key positions in all the major companies across the world influencing strategic decisions in these countries2. The penetration of Chinese spin doctors in the international media is wide and deep. Bulk of the countries in the European Union is targeted by China. Major international media platforms such as BBC, Washington Post and New York Times are influenced by Chinese financial clout. China’s media warriors have good hold over American Corporations3. This helps in all types of cyber-attacks ranging from creating desired public opinion in the target group to abetting other cyber espionage including denial of service attack to disruptive and destructive cyber-attacks.
At the military level the People Liberation Army (PLA) has combined electronic war fare and computer network attack into the concepts of Integrated Network Electronic Warfare (INEW). These units in the PLA are designed to attack the enemy military cyber space and electronic systems using appropriate cyber weapons. Besides, China has raised Unit 61398 for carrying out most extensive cyber-attacks across the globe. This unit conducts attacks on military as well as non-military targets4.
As per the observed trends of Chinese cyber war activities it appears that the highest priority is given to manipulating public opinion, propaganda, suppression of public opinion against the Chinese Communist Party both at home and abroad and conducting media war. Somewhat similar priority is given to cyber theft, denial of service and disruption/ destruction of target networks. In case of military conflict the PLA can use external cyber weapons (also known as type 2 weapons that is being discussing later). However use of type 2 weapons is not very common due to ease of attribution and quick retaliation. Most of the times, internal weapons (known as type 1 weapons discussed later) are used that defy accurate and quick attribution.
India’s Quest for Cyber Deterrence and Global Perspective
On 12 April 2019 a task force of Vivekananda International Foundation (VIF) presented a report on, ‘Credible Cyber Deterrence in Armed Forces of India’ to the then Raksha Mantri (Ms Nirmala Sitharaman)5. During 2019 and 2020 the Govt. of India initiated several actions ranging from restructuring the National Security Structure, raising organizations to safeguard India’s cyber space. The need for these restructuring and strategic organizations was felt almost two decades back since major military powers- specifically China (as we have seen earlier), had invested heavily in this domain. Cyber space for China was the chosen turf for unrestricted warfare.
At the global level the US was the first nation to raise a Cyber Command with formidable cyber offensive capabilities. This happened during the late nineties. President Trump’s administration revised their military doctrine stating that any attack on the US cyber space will be considered as an attack on the US sovereignty and will be punished militarily. Israel had Unit 8200 that participated in deadly cyber-attacks on Syria and Iran in collaboration with the US. The UK established Joint Forces Cyber Group and Joint Cyber Reserve Force. The Dutch Ministry of Defence established a Cyber Command with offensive and defensive capabilities6. The Russians conducted Cyber-attacks on Estonia and later on Chechnya. These are just few examples that signify the fact that the Cyber space was becoming a precious domain and every country of some relevance wanted to deter their prospective adversaries from causing harm to their respective cyber spaces. The concept of cyber deterrence had gained phenomenal importance and popularity.
Concept of Cyber Deterrent and Policy of Deterrence: Relevance and Reliability Aspects
A cyber deterrent is specific technique or measure to deter the enemy/ adversary/criminals from threatening or attacking own cyber space. Deterrents can also be covert or overt military operations as retaliation. Cyber deterrence entails formulating strategic approaches, policies and processes to restrict cyber-attacks on our cyber space. Deterrents propagate or demonstrate costs to the attackers when they plan or think of attacking cyber space. Deterrence involves political will, extent of damage to be caused on the criminal/attackers. It also involves international cooperation and issues related to organizations, hierarchies and knowledge base related to cyber offensive. Deterrence should also lay down doctrines, policies and scale of military operations in retaliation to a cyber-attack. How do we develop specific deterrents and evolve a China centric policy of deterrence?
To understand the concept of deterrence we may look at nuclear deterrent of the cold war era. The policy of nuclear deterrence was based on the basic premise of preventing major threat to national security from an adversary (assumed to be much more powerful) specifically if the adversary possessed nuclear weapons. Five decades after the concept became popular a large number of leaders and national security professionals have started realizing the weaknesses of the concept of Mutual Assured Destruction (MAD). It is not our objective to examine the frailties of nuclear deterrence. But in the context of what nuclear deterrence meant we can analyze the concept of cyber deterrence.
Here are some interesting facts. The US is among the top most wired nations. It also has the most powerful Cyber Command (besides possessing most powerful military) for launching cyber- attacks. Ironically it also tops the list of nations that are subjected to maximum number of cyber espionage attacks on a daily basis. In case of China the situation is more confusing. While China tops the list of nations from where maximum distributed denial of service originate its own networks have maximum malware infections- 49 percent malware infection in Chinese cyber space. Among the most vulnerable nations against cyber-attacks China ranks at number five. India though tops the list of nations where the cyber space the gets maximum impact from ransom ware it still fares better than China7. Chinese capability and propensity for attacking cyber space of other nations equals or surpasses that of the US. Among the least threatened nations in the cyber space are perhaps Afghanistan and South Sudan. Because they their use of cyber space is minimal.
Thus, even if a nation has the most powerful cyber-attack capabilities it still can be subjected to cyber-attacks. The only way to be entirely immune to cyber threats is to not use cyber space at all-an option no sensible nation would opt for. So what is the relevance of creating cyber deterrent based on cyber offensive capabilities?
Complexities in Formulating Strategies for Cyber Deterrence
The above discussion leads us to think that the concept of cyber deterrence is not linear. We need to look at three very distinct issues before we formalize our plans for creating cyber deterrence. First the exceptionally massive – and ever increasing contribution of Information and Communication Technologies (ICT) in almost all areas that affect the lives of citizens- wealth creation, governance, health, education, social interaction etc. to name a few. This necessitates creation, expansion and exploitation of cyber space as a continuous process. Secondly, though the cyber threats are real these are graded. Some of these threats are much less harmful than some other threats that can be devastating. This brings us to the graded cyber security. Thirdly, the sources of cyber threats need to be monitored and if need be neutralized. Also in a volatile and imperfect world nations do indulge in offensive actions in pursuance of their national policies. These offensive activities on own cyber space need to be minimized by instilling adequate fear in the minds of the attackers. The attacker must be made to bear prohibitive costs for any cyber misadventure on own cyber space. This is where the deterrence comes in. Thus we have three major issues to address when we formulate policies for cyber deterrence
- Maximize the pay offs from adaption of Cyber space for well-being of the citizens.
- Create appropriate cyber security architecture with focus on China. This will ensure that while we get maximum pay offs from ICT adaption, the damages to the cyber space are minimized. The cost benefit ratio must favour ICT adaption and not inhibit us from harnessing the cyber space for phenomenal all round gains.
- Create cyber offensive capabilities to deter the prospective attacker.
Pay Offs from Exploitation of Cyber Space for well-being of the Citizens
The Global Competitive Index (GCI) prepared by the World Economic Forum (WEF) considers ICT adaption as one of the twelve pillars of competitiveness of a country. Their 2019 report that covered 141 nations compares ICT adaption with the overall rankings of respective nations. We may look at the correlation between the global competitiveness of some of the nations with their respective rankings in ICT adaption- which is based on broadband penetration, mobile connections, and use of internet, broad band and internet speeds etc8.
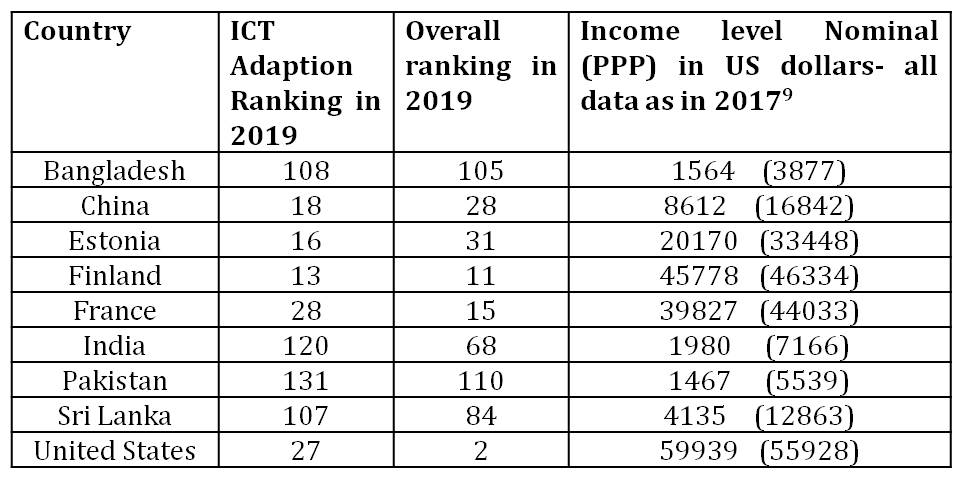
The table reveals a very close correlation between the ICT adaption and competitiveness of the concerned country. Also see the close relation between the GDP per capita and ICT adaption. In case of India the findings of the WEF are surprising. India is known for its global competitiveness in terms of ICT industries. We also have the best human capital in this field. Our overall ranking at 68 in 2019 is a marked improvement over what we were six years back. But the ICT adaption ranked at 120 is a ‘pull down’ effect. If India focuses on ICT adaption our global competitiveness in other pillars is likely to show remarkable improvement. Hence, if our leadership wishes to propel India to a five trillion dollars economy during the next four years then massive and innovative exploitation of ICT appears to be the best bet. When we do so an effective cyber deterrence to protect our cyber space becomes equally important.
In the context of our subject we need to go deeper into the notion of ICT adaption. A discussion paper prepared by the International Telecommunication Union (ITU) in August 2020 describes digitization as ‘transformation of techno-economic environment and socio-institutional operations through digital communication and application’10. This in essence means creating a robust, country wide cyber space endowed with high speeds ( the developed nations have started using 5G speeds- gigabits per second, in 39 percent of their networks) with easy access and equipped with desired applications for governance, commerce, health, production, education and so on). The report makes another revelation. Countries with per capita income less than 12000 US Dollars will show the steepest growth in GDP- almost 2.5 percent with an increase of 10 percent growth in mobile broad band penetration11. Beyond this income level growth is more closely correlated to fixed line broad band penetration. Out of 139 countries surveyed by the ITU, 63 countries fall in lower than $12000 per capita. Hence, for the purpose of our discussion the poor countries of the world have no option but to expand, modernize their respective cyber spaces and start using these innovatively for the wellbeing of their citizens. In case of India, the Communications, IT and Law Minister Shri Ravishankar Prasad -while speaking at the Sixth ET start up awards 2020, was confident that the digital India and digital ecosystem will add one trillion dollars to the Indian GDP12 (envisaged to be around five trillion dollars by 2024).
Strategic Vision for Cyber Deterrence, Defensive- Offense
The VIF Task Force Report quoted above recommended building up cyber power supported on the seven pillars of doctrine, policy, organizations, human resources, technology, and integration of cyber power with cyber deterrence and international engagement along with legal framework. The Task Force confined itself to the Indian Armed Forces keeping in view the scope of the study. Hence, the deterrence policies addressed issues related to military operations. However, bulk of Chinese offensive is directed at the civilian targets- public opinion, critical Indian institutions, banking services, media houses and so on. Secondly, we have seen earlier irrespective of what cyber power a nation builds up- cyber attacks on own cyber space (civilian as also military) will continue. If this be so then do we need cyber power and cyber deterrence? Yes we do. But the contours and the concepts of cyber deterrence will be different than what we envisaged for nuclear deterrence. The strategic vision for cyber deterrence must be based on ‘defensive - offense’. It is impossible to deter even an ordinary cyber-criminal to attack our cyber space since it is so easy to commit cyber- crime and attribution is so difficult. An exceptionally large number of cyber-attacks are not even noticed. Equally large numbers are not even reported. In case of propaganda, misinformation, manipulating public opinion, creating unrest in the country using social media tools (an extension of cyber space in the fourth and fifth generation cellular communication), and media war conducted by China the task becomes extremely complex and difficult in a democracy like India. Thus the ‘defensive-offence’ will have to be adopted at all the three levels- cognitive, software and hardware.
Cognitive Level
With the advent of easy to use social media platform like Face Book, WhatsApp, YouTube, Twitter and the like the cyber threats at the cognitive levels of the population becomes very dangerous. With mobile phones at 4G-and very soon 5G, speeds and the comparative ease with which the phones can be used even by an illiterate person the reach of cognitive level cyber threat extends to every individual. Uploading pictures, texts, videos that destroy social harmony, swing preferences of the voters (in a democracy) becomes very easy. Social media can very easily spread rumors, half-truths, blatant lies. Regulating the social media in democracies like the US and India is extremely difficult. Hence, the cognitive deficiencies among the common citizens can be very easily exploited by criminals and nations to harm the adversary. Chinese objectives in targeting India at this level are to manipulate public opinion, spread misinformation, dilute the efficacy of Indian institutions especially the judiciary, media and political systems. China would expect to create unrest in various parts of India, slow down the Indian economy as also obstruct reforms to blunt India’s competitive edge in international power equilibrium. While the objectives are as old as the history of Sino Indian conflicts starting from 1949 (Chinese design on Tibet) the means adopted to achieve these objectives have improved dramatically.
Chinese support to the ongoing Naxalite movement by exploiting the inherent weaknesses in our judicial system, their support to anti –Citizenship (Amendment) Act (CAA) through the principal opposition political party in India, that culminated in Delhi Riots, the ongoing movement against the Farm Sector Bills are just a few examples of Chinese involvement in Cyber offensive against India through social media. These offensives did have adverse impact on India in terms of economic loss (lower productivity), unrest among the people thus denting the social capital of the country, adverse international effect and so on. What type of deterrence can we have against such an offensive? Based on our strategic approach of defensive offence the priority sector in this case would be prophylactic cover against Chinese offensive at cognitive level.
In a democracy like India this seemingly simple task is most difficult and complex of all other measures to secure the nation in the cyber space. The protective cover against cognitive level cyber-attacks would need exceptionally vibrant, citizen centric, transparent and participative democracy, high standards of political leadership as also harmonious social capital. At the same time this would need high levels of investments in education and awareness on national heritage, national security and creating free analytical minds that can see through real inefficiencies and propaganda. Technologically the government needs to regulate and control the social media platforms for the purpose of identifying, stopping potentially harmful contents.
Measures need to be taken to localize national data flowing through the social media and Internet. Effective cyber forensic along with modern judicial system to identify and punish the cyber -criminals abusing the social media platforms will become very necessary. For obvious reasons people in the Indian democracy will oppose regulation and censorship. This is where the political leadership needs to get together and balance out need for freedom of speech, citizens’ privacy along with national security. While emphasis is placed on security or defensive measures we need to build up adequate offensive capabilities against China at this level. Behind the façade of a unified powerful and highly disciplined China lies a society seething under an authoritarian and totalitarian regime. There are well known insurgencies in China- the Uyghurs, the Mongols and the Tibetans who are at logger heads with the majority Han population. A highly controlled and internally fragmented society is prone to implode. We see this in Hong Kong.
The Chinese leadership appears to be fully aware and hence sensitive to these threats. Since China has traditionally fished in our troubled waters with impunity India need not hesitate in sending a return gift. Deterrents at this level need to be designed and used at the highest level. The organization to implement the offensive would need multidisciplinary teams from the media, computer Science (Artificial Intelligence, Big Data), ‘China experts’, psychologists and so on. Such campaigns are conducted in a sustained manner over a reasonable time frame to drive home the message. Once China realizes the adverse impact of such a campaign they will be deterred to conduct the cognitive level attacks on India with impunity.
Software/ Logical Level
Primarily two types of cyber weapons are used at the logical level based on their existence within the cyber space or used externally. The ‘internal’ weapons can be defined as ‘computer codes that are used or designed to be used with the aim of threatening or causing physical, functional or mental; harm to structures systems or living beings’ (Rid)13. In essence these can be used for stealing information, disruption or denial of services provided by the network or disrupting/destroying the platform/device/structure connected to the network through Supervisory Control and Data Acquisition (SCADA). The external weapons are primarily designed to create electromagnetic flux powerful enough to damage or cyber networks- which are generally very sensitive to high voltages. The external weapons are generally in the domain of national militaries due to the type of resources required for creating the effect.
Though, terrorist organizations can also procure these from countries that support the terrorist organizations. For details the reader may either use open network resources or refer to pages 370 and 371 of the India’s Strategies …..14. This part of cyber space is targeted by ordinary cyber criminals for fun, monetary gains as also by trained professionals sponsored by hostile nations for surveillance, stealing information, and denial of services, disruption and even destruction. The attackers exploit various software related vulnerabilities in the cyber space to achieve their respective objectives. As regards specific threat from China The Indian Home Secretary Shri Rajiv Gupta while speaking at Federation of Indian Chamber of Commerce and Industries (FICCI) on 31 May 2018 observed that China is a major aggressor on the Indian cyber space and bulk of the cyber-attacks are on ONGC, IRCTC, NIC, Center for Railway Information System, Punjab National Bank, State Bank of India, Oriental Bank etc. Geographical locations of these attackers are in Maharashtra, Madhya Pradesh and Karnataka15. It will be appropriate to look at the vulnerabilities and ways to plug these as cyber security protocols/procedures:-
- Structure. When the internet opened up- from defence and academic use, to commercial and societal proliferation the emphasis was on accessibility, inter-operability, speed, versatility and fastest rates of expansion. Authenticity, credibility of information, restrictions to access for security reasons and above all regulation by the governments had no priority. No one visualized that criminals, perverts, anti-social elements etc. will use the internet to harm others. It was also unimaginable at that time that nations will use it to attack other nations. Thus the primary vulnerability of the internet is in its structure itself. To minimize the vulnerabilities the users, service providers, experts, institutions and the government need to work together. Basic education to the users on elementary cyber security, modular architecture of the network that can be quickly isolated from the infected part with the use of network devices, constant reading of the packets flowing through various routers and switches to check for uncommon traffic, high grade cyber forensic, adequate cyber security experts in each organization that uses cyber space for its functioning, strengthening the Central Emergency Response Team (CERT) are some of the measures that can mitigate structural vulnerabilities.
- Software Design. The internet is operated through software designed by humans. Writing software for a wide range of utilities- some of these being very complex is a tedious task. In case very highly skilled software engineers are employed to write software that cannot be breached the cost of the software becomes too high. Any dilution in the quality of people writing the software compromises the security of the network. Big MNCs generally work on profit orientation based on cutting costs on human resources. Thus the quality of software is not too secure. Besides at times deficiencies in the software is intentional for obvious reasons. India has adequate expertise in software design. We need to create adequate talent pool in the country to design, test and upgrade software needed for our sensitive and critical requirements.
- Open versus Close Source Operating Systems. Open source operating systems are available for free and the source codes can be viewed by any user. The user can also modify the system or fix some deficiencies. In the closed source the source code of the operating systems are available for a fee. Here the operating systems are for profit. How does it concern network security? In as closed source operating system the bugs or discrepancies (that can be used by the hackers) are to be found by the third party that buys the system. Since the systems are written for profit- cost cutting by employing less proficient code writers is common. Vulnerable operating system that cannot be fixed by the user (since they do not know the source code) adds to the security concerns. We need to move towards Linux based open source systems with suitable modification based on our own requirement. In case we decide to remain with the closed Microsoft systems then it is important to get the source code and fix responsibilities if vulnerabilities are noticed in the software.
- Platforms, Network Components and Service Providers. The ‘things’ of internet- weapon platforms, home appliances, industry plant etc. also function on hardwired and software driven codes. Any discrepancy here leads to security threat. Service providers of the company that sells these ‘things’ or platforms can leave bugs in the systems intentionally. This aspect needs to be addressed at the time of procurement.
- Level of Awareness of the Users. Bulk of literature on cyber security vulnerability declares that more than eighty percent of security breaches occur because of lack of awareness, carelessness or willful default by the users. This is where very large scale training in basic levels of cyber security becomes so pertinent.
Hardware/ Physical Level
Network Components: To derive maximum payoffs from the cyber space it must proliferate to all corners and all individuals in the state. A very large quantum of network components is needed for this expansion. These devices- routers, switches, bridges, desk tops, Wi Fi devices are potential points of beach of cyber security if adequate cyber security measures are not adopted. In our enthusiasm to speed up the proliferation security aspects are neglected. Hence, installation of cyber security measures along with continuous training to remain updated should become part of the proliferation process.
Internet of Things: As the bit rates per second flowing through the internet grew at dramatic pace the ‘things’ that could be manipulated by SCADA systems increased. As Internet of Things (IoT) grew so did the threats to the things that were connected to the net. From denial the threats escalated to disruption and destruction. The ease of functioning needs to be weighed against the security threat and level of damage or destruction that can be caused by disruptive/destructive cyber-attack. In very sensitive cases it may be advisable to prefer security over ease. If SCADA system is inevitable then monitoring and functioning procedures must be adhered to most strictly.
Global Supply Chains: The increasing complexities of products and services transformed operations management to supply chain management where each product or service was made of increasing number of components produced in different enterprises, nations across the continent. The new system of production termed as supply chain management entailed independent entities collaborating and cooperating to produce common goods or services through strategic use of the internet. It became easy for enterprises and nations to hide dormant cyber weapons in their products or services for use at an opportune time. The Kill Switch attack on the Syrian Nuclear Reactor by Israel is an example how the supply chain vulnerability was exploited this weakness.15 Cyber-attack risks emanating from the vulnerabilities of the supply chains can be mitigated by highly specialized software and hardware analysts the check these at the time of procurement and subsequent upgradation. Ideally sensitive supply chains need under own control or should be jointly managed.
Conclusion: Recommendation for Cyber Deterrence
Our approach to cyber deterrence needs to be based on the doctrine of ‘defensive offence’. In the context of cyber threats from China the policy needs to be monitor, deny, detect, analyze, attribute, launch focussed attack, monitor impact, and modify attack till desired effect is achieved. These actions may overlap and will comprise of:
- Monitor-Report. Constant and diligent monitoring of all cyber space by all users and trained operators who are capable of sensing the occurrence of cyber-attack in their respective systems and net-works. This would include each device connected to the internet including the mobile and ‘things’ on the internet as also Local Area, Wide Area and Country Wide networks. This would entail very large scale training in cultural and technical aspects of cyber security at two levels. First at the level of each individual user and second the cyber security operator at the organizational/institutional /levels. Smallest breach or damage to the system/device or the networks must be reported to a designated agency in the organization that in turn notifies the national agencies set up for monitoring cyber-attacks on Indian cyber space. Teams comprising of highly trained experts in multi discipline domains would be need to monitor the social media part of cyber space.
- Deny. Having sensed cyber-attack or breach of cyber security the first immediate action must be to cleanse the system or the device, isolate or close the network and deny proliferation of the damage to other networks. This will limit the extent of the damage. Sooner the denial activities start lesser will be the impact of the cyber-attack.
- Detect and Analyze. During the monitor stage the symptoms of the attack like slowing down of the system/device/network or theft of information/financial fraud /defacing of the website, phishing etc. will be noticed. This is something which the user or network manager with very basic knowledge of cyber security will be able to identify. Beyond this the detection and analysis team would work out the type and possible origin of the attack. The attack may be through worms, bacteria, Trojans, logic bombs, virus, and trapdoors. This attack could be an insider work, by a trained professional or amateur cyber-criminal. In the context of cyber-attack through social media platforms the attacker could be from insider lobby, terrorist organization, political party, media professionals of enemy countries, international organizations that perform these tasks as mercenary organizations. In the ‘detect and analyze’ part the team will detect the type and likely offender.
- Attribute. This is the most complex and sensitive part of the cyber security activities. The current technologies provide the attackers capabilities to mask the attack behind a number of technical screens that make the attribution difficult. Besides the external enemy can very easily use internal resources of the target country to launch the attack. The attack could also be launched from a third country with or without their approval. The attacker can adopt crowd sourcing where a very large number of individuals take part in the cyber offensive. Thus attribution would need close cooperation among number of experts from a large number of institutions at times spread over a few countries. Thus even after sensing the attack and analyzing the data pertaining to the attack attribution will take time and most often will be difficult to prove in a court of law based on the old Evidence Act. There may be occasions when it may not be prudent to disclose the attribution to the public.
- Cyber Counter Attack. This is the offensive part of the defensive-offence strategy of cyber deterrence. It works at two levels. First for the internal or insider offenders/criminals. This would involve quick detection, attribution framing of charges and conviction in such a manner that the punishment acts as a deterrent for other criminals. As an example Singapore awards death penalty to drug traffickers. A habitual cyber criminal or an insider abetting external agencies/nations to harm India through the cyber space must get such a stringent punishment in quick time frame so as to deter others from such an act. An insider abettor must be treated as a foreign spy or part of threat to national security. This aspect of deterrence would need thorough overhaul of our existing jurisprudence and current narrative of freedom of speech/protest/expression that allows individuals and groups to get away with very major infringements on national security through the abuse of cyber space. The second level of cyber deterrence would be directed specifically towards the external aggressors such as China. At present 35 percent of cyber-attacks on the Indian cyber space are from China or China inspired agencies17. Since very large part of the visible cyber attack is through social media or generic media platforms we need to work on the well-known weaknesses of China where media war and social media offensive can be easily launched. Thus well-orchestrated narratives on Taiwan, Hong Kong, Tibet, Uyghur, Mongols can be formulated for waging prolonged offensive against China. Add to this the opportunities provided by internal turbulence against the high handedness of the Chinese Communist Regime against the common Chinese citizen. Such an offensive must continue till we see discernible reduction in the number of Chinese or China sponsored attacks against India. At technical level we need to analyze the Chinese cyber space for weaknesses and place suitable cyber weapons at various network junctions to be used at opportune time. Similarly, insider abettors must be cultivated within China and other friendly nations to launch retaliatory cyber-attacks on the selected parts of Chinese cyber space. Sustained implementation of such a strategy may make China amenable to negotiate relevant treaty with India for honouring each-others’ cyber space. China has signed such a treaty with Russia, though they declined to sign similar treaty with the US.
To operationalize the above strategy immediate measures need to be taken across a wide spectrum of national domains. Firstly, to prepare highly aware users of the cyber space and skilled operators who can monitor and sense cyber attack massive impetus will have to be given on relevant study of the cyber security issues. This needs to be treated at par with basic literacy, primary and secondary level training and education. Since the types, patterns, techniques and tools used for cyber-attack change very fast this initiative needs to be updated every two years. While the bottom of the pyramid is prepared to sense and plug the cyber -attack the tertiary level training and education must cater for personnel who can detect the type of attack and analyze the source as also the motives. This would involve emphasis on computer science, psychology, sociology, mass communication, political science, cyber forensic, criminal law etc. so that the analysis team has complete grasp of the attack. This team will then suggest counter actions either in terms of gathering sufficient evidence for dealing with the cyber-crime or a cyber counter offensive on the country/groups to deter further attack. It may be relevant to mention here that China established four universities as early as 1999 to study and conduct research on cyber war18. These universities produce personnel and domain knowledge to compete in the cyber space. At the functional level large scale and deep reforms will be required in our judicial, administrative, law enforcement organization and most importantly in the political system that controls all these pillars of nation building and national security.
End Notes
- Ashok Pathak India’s Strategies for Information War & Cyber Deterrence, Vitasta Publishing Private Limited Ansari Road Daryaganj 2020 ISBN 78386473875
- https://www.infosecurity-magazine.com/news/data-leak-chinese-communist-party/
- https://www.orfonline.org/expert-speak/chinese-sharp-power-is-beijing-influencing-public-opinion-in-india-57779/
- Ibid 1
- https://www.vifindia.org/sites/default/files/Credible-Cyber-Deterrence-in-Armed-Forces-of-India_0.pdf
- James A Green (Editor) Cyber Warfare: A Multidisciplinary Analysis, Routledge Taylor & Francis Group (2015) ISBN 978-1-138- 79307-1
- https://www.cybersecurity-insiders.com/list-of-countries-which-are-most-vulnerable-to-cyber-attacks/
- http://www3.weforum.org/docs/WEF_TheGlobalCompetitivenessReport2019.pdf
- https://www.worldometers.info/gdp/gdp-per-capita/
- https://www.itu.int/en/ITU-D/Conferences/GSR/2020/Documents/ITU_Global_Econometric_Modeling_GSR-DiscussionPaper.pdf
- Ibid 1
- https://telecom.economictimes.indiatimes.com/news/electronics-manufacturing-can-contribute-1-trillion-to-indias-economy-by-2025-prasad/79794792
- Rid Thomas, Cyber War Will Not Take Place, C Hurst & Co Publishers 2013, ISBN: 978-1-84904-280-2
- See ibid 1.
- Rajiv Gupta (Home Secretary), while speaking at FICCI on ‘Smart Policing Partnership with Corporate and Academia’ ( www. indiatoday.in 31 May 2018)
- Clarke A Richard and Knake Robert K, Cyber Warfare: The Next Threat to National Security and What to do About it, Harper Collins Publishers, 10 East 53rdStreet New York 10022, First Edition 2010 ISBN 978-0-06-196223-3
- Ibid 1
- Institute of Defence Studies and Analysis (IDSA)Task Force Report March 2012, ‘India’s Cyber Security Challenge
(The paper is the author’s individual scholastic articulation. The author certifies that the article/paper is original in content, unpublished and it has not been submitted for publication/web upload elsewhere, and that the facts and figures quoted are duly referenced, as needed, and are believed to be correct). (The paper does not necessarily represent the organisational stance... More >>
Image Source: https://images.moneycontrol.com/static-mcnews/2021/03/India-China-747x435.jpg?impolicy=website&width=770&height=431










Post new comment